Invoice fraud is hitting businesses harder every year, and the numbers prove it. Companies lose up to 5 percent of annual revenue to various fraud schemes, according to recent studies. Most think cybercriminals must be using wild technology tricks or complex hacking. Actually, the biggest risk is often much simpler and starts with just one faked invoice slipping past a tired employee.

How to Prevent Invoice Fraud: Practical Steps for Businesses
Table of Contents
- Recognizing Common Invoice Fraud Schemes
- Essential Policies To Prevent Invoice Fraud
- Best Practices For Secure Invoice Processing
- Using Technology To Reduce Invoice Fraud Risk
Quick Summary
| Takeaway | Explanation |
|---|---|
| Implement rigorous verification processes | Establish strict protocols for verifying vendor authenticity and invoice details. This reduces the risk of payments to fraudulent entities. |
| Adopt segregation of duties | Divide responsibilities among employees for invoice approvals and payments to prevent collusion and unauthorized actions. |
| Utilize technology for fraud detection | Leverage AI and machine learning to identify anomalies in invoices, enhancing detection of potential fraud before payments are made. |
| Maintain standardized documentation practices | Implement clear guidelines for invoice documentation, ensuring auditable trails that make manipulation difficult and easily identifiable. |
| Continuously educate employees on fraud | Regularly train staff on emerging fraud techniques and encourage reporting of suspicious activities to cultivate a proactive fraud prevention culture. |
Recognizing Common Invoice Fraud Schemes
Invoice fraud threatens businesses of all sizes, with criminals constantly developing sophisticated methods to exploit financial systems. Understanding these deceptive tactics is the first critical step in protecting your organization from potentially devastating financial losses.
Phantom Vendor Schemes
Phantom vendor fraud represents one of the most insidious invoice manipulation strategies. Fraudsters create fictitious companies that submit seemingly legitimate invoices for nonexistent goods or services. According to the United States Postal Inspection Service, these scams often rely on exploiting weak verification processes within organizations.
Tactical criminals might register fake businesses with convincing documentation, complete with fabricated tax identification numbers and contact information. They strategically design invoices that appear normal at first glance, using subtle techniques to bypass initial review processes. Small details like slightly altered company names or marginally different letterhead can slip past hurried accounting staff.
Invoice Alteration and Manipulation
Another prevalent fraud scheme involves manipulating legitimate invoices through careful modifications. The Association of Government Accountants highlights how perpetrators adjust invoice amounts, duplicate existing documents, or insert unauthorized line items.
Common manipulation techniques include:
- Price Inflation: Subtly increasing unit prices or total amounts
- Duplicate Billing: Submitting identical invoices multiple times
- Unauthorized Additions: Inserting extra services or products not originally agreed upon
These modifications might seem minor but can represent significant financial risks when accumulated over time. Fraudsters often target organizations with decentralized accounting systems or limited cross-referencing capabilities.
Advanced Digital Fraud Techniques
Modern invoice fraud has evolved beyond traditional paper-based methods. Cybercriminals now leverage sophisticated digital techniques that exploit technological vulnerabilities. They might use advanced email spoofing, create convincing digital replicas of legitimate vendor invoices, or deploy social engineering tactics to manipulate payment workflows.
Technical approaches include generating invoices that mimic the exact formatting of trusted vendors, using compromised email accounts to send fraudulent documentation, or exploiting gaps in digital payment verification systems.
To protect against these intricate schemes, businesses must develop robust, multi-layered verification processes. Learn more about comprehensive invoice verification strategies that can help safeguard your financial systems against these evolving threats.
Recognizing these fraud schemes requires constant vigilance, systematic verification, and a proactive approach to financial documentation management. By understanding the tactics criminals employ, organizations can implement more effective preventive measures and minimize their vulnerability to invoice fraud.
To help you quickly recognize and compare the main invoice fraud schemes discussed, here is a summary table outlining their key characteristics and tactics used.
| Scheme Type | Key Characteristics | Common Tactics Used |
|---|---|---|
| Phantom Vendor Schemes | Creation of fake companies to submit invoices for nonexistent goods/services | Fake business registration, fabricated documents, subtle name/letterhead changes |
| Invoice Alteration & Manipulation | Modification of legitimate invoices to inflate or duplicate payments | Price inflation, duplicate billing, unauthorized additions |
| Advanced Digital Fraud Techniques | Use of digital/wire fraud to exploit technology and organizational vulnerabilities | Email spoofing, vendor invoice replicas, payment workflow manipulation |
Essential Policies to Prevent Invoice Fraud
Preventing invoice fraud requires a comprehensive and strategic approach that goes beyond simple reactive measures. Organizations must develop robust policies and systematic controls that proactively identify and mitigate potential financial risks before they escalate.
Establishing Rigorous Verification Protocols
Effective invoice fraud prevention starts with implementing stringent verification processes. According to the U.S. Government Accountability Office, robust internal controls are critical for preventing improper payments and financial misconduct. This means creating a multilayered verification system that scrutinizes every invoice before payment.
Key verification steps should include:
Below is a process table outlining key verification steps businesses should implement, as detailed in the section on stringent verification protocols. This serves as a reference for strengthening invoice approval workflows.
| Verification Step | Description | Purpose |
|---|---|---|
| Vendor Authentication | Conduct comprehensive background checks on new vendors | Ensure vendor legitimacy |
| Cross-Referencing | Match invoices against original purchase orders | Confirm goods/services were authorized |
| Contact Confirmation | Independently verify vendor contact information | Prevent communications with fake vendors |
| Pause, Verify, Report (PVR) | Stop and validate invoice details using existing contact info | Prevent hasty or improper payments |
- Vendor Authentication: Comprehensive background checks on new vendors
- Cross-Referencing: Matching invoices against original purchase orders
- Contact Confirmation: Independent verification of vendor contact information
The Massachusetts Office of the Comptroller recommends adopting a ‘Pause, Verify, Report’ (PVR) protocol. This approach encourages financial teams to stop and thoroughly validate invoice details using pre-existing, independently confirmed contact information before processing any payments.
Implementing Segregation of Duties
One of the most powerful defensive strategies against invoice fraud is establishing clear segregation of duties within financial departments. Columbia University Irving Medical Center’s Fraud & Abuse Policy emphasizes the critical importance of educating employees about fraud prevention and establishing distinct roles that prevent any single individual from having complete control over financial transactions.
Effective segregation might involve:
- Separating invoice approval from payment processing
- Requiring multiple approvals for transactions above certain monetary thresholds
- Rotating financial responsibilities periodically to prevent potential collusion
- Implementing mandatory vacation policies for finance personnel
These strategies create natural checks and balances that significantly reduce the risk of internal fraud and unauthorized financial manipulations.
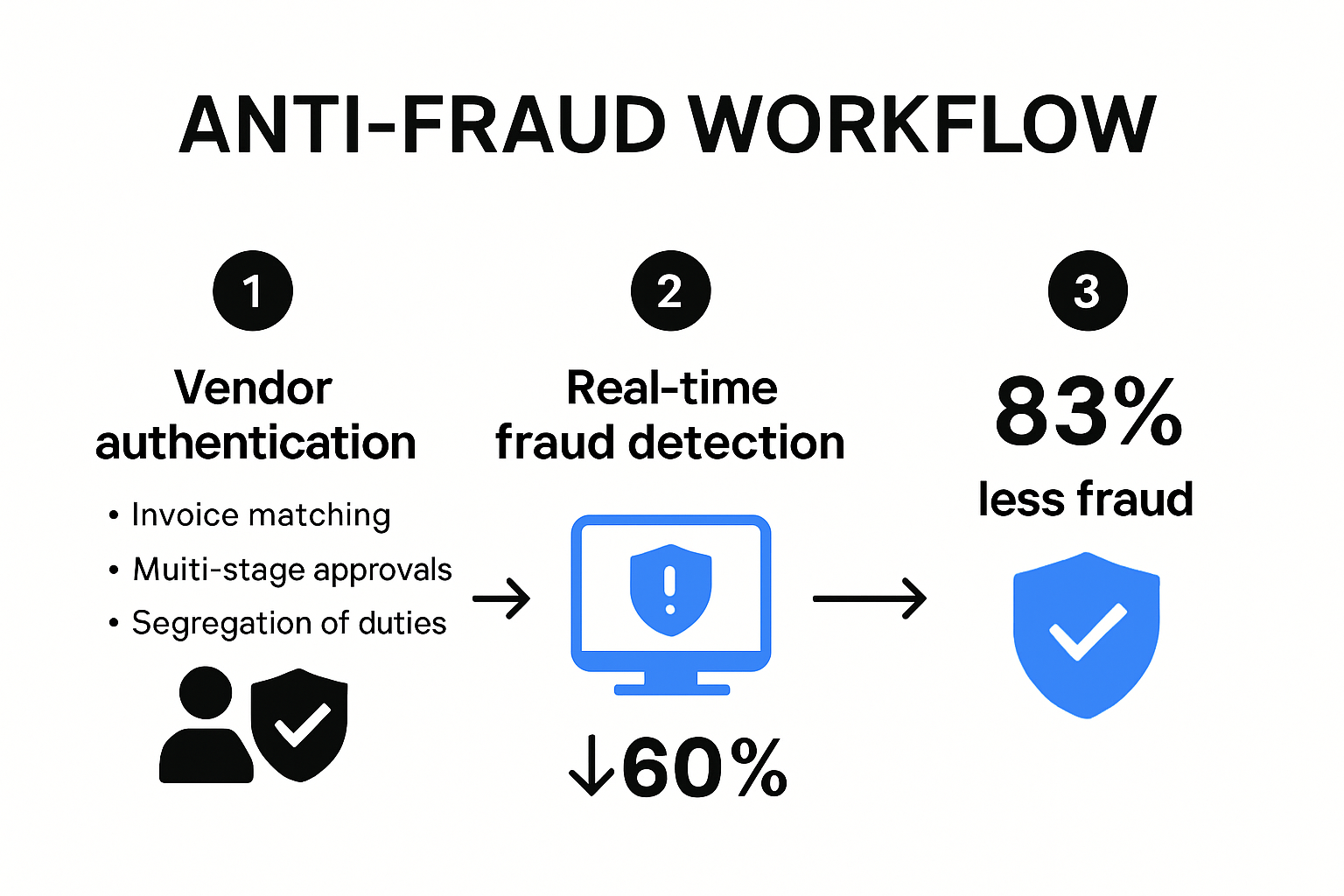
Technology and Continuous Education
Modern invoice fraud prevention requires a combination of advanced technological solutions and ongoing employee education. Learn more about comprehensive invoice verification techniques that leverage artificial intelligence and machine learning to detect anomalies.
Companies should invest in:
- Advanced Detection Software: Tools that use AI to identify suspicious invoice patterns
- Regular Training Programs: Workshops that keep staff updated on emerging fraud tactics
- Transparent Reporting Mechanisms: Clear channels for employees to report potential fraudulent activities without fear of retaliation
By combining technological solutions with human vigilance, organizations can create a dynamic and adaptive fraud prevention ecosystem. The goal is not just to detect fraud but to create an organizational culture that actively resists and prevents financial misconduct.
Remember that invoice fraud prevention is an ongoing process. Regular policy reviews, technological updates, and continuous staff training are essential to staying ahead of increasingly sophisticated fraudulent techniques.
Best Practices for Secure Invoice Processing
Secure invoice processing is a critical defense mechanism against financial fraud, requiring strategic approaches that combine technological solutions with meticulous organizational practices. Businesses must develop comprehensive systems that protect financial integrity and minimize vulnerability to potential manipulation.
Standardized Documentation and Verification Protocols
Consistent and rigorous documentation represents the foundation of secure invoice processing. According to the U.S. Department of the Treasury, establishing clear guidelines for invoice documentation is essential in preventing fraudulent activities.
Key documentation standards include:
- Invoice Numbering: Using unique, sequential alphanumeric identifiers without special characters
- Service Period Specification: Clearly defining exact service dates and delivery periods
- Comprehensive Vendor Information: Maintaining complete and updated vendor records
These standardized practices create an auditable trail that makes unauthorized modifications significantly more difficult. By implementing systematic documentation protocols, organizations can quickly identify and investigate potential irregularities.
Internal Control and Workflow Management
Effective invoice processing demands robust internal controls. The University of California, Davis emphasizes the critical importance of separating financial responsibilities to prevent potential fraud.
Recommended workflow management strategies include:
- Role Segregation: Distributing financial tasks across multiple team members
- Multi-Stage Approval Processes: Requiring multiple independent verifications
- Regular Reconciliation: Conducting frequent and thorough financial reviews
- Digital Audit Trails: Maintaining comprehensive electronic records of all transactions
By creating layered verification mechanisms, businesses can significantly reduce the risk of unauthorized financial transactions and detect potential fraudulent activities more effectively.
Technology-Driven Invoice Processing
Modern invoice processing leverages advanced technological solutions to enhance security and efficiency. Learn more about streamlined invoice data management that integrates cutting-edge verification techniques.
Advanced technological approaches include:
- Automated Verification Systems: Using AI to cross-reference invoice details
- Machine Learning Anomaly Detection: Identifying suspicious patterns in financial transactions
- Secure Cloud Storage: Maintaining encrypted digital records with restricted access
- Real-Time Monitoring: Implementing continuous transaction surveillance
Technology transforms invoice processing from a reactive to a proactive approach. Automated systems can instantly flag potential discrepancies, allowing financial teams to investigate and respond rapidly.
Ultimately, secure invoice processing is not about implementing a single solution but creating a comprehensive, adaptive strategy. Organizations must continuously evolve their practices, integrate advanced technologies, and maintain a culture of financial vigilance to effectively mitigate invoice fraud risks.

Using Technology to Reduce Invoice Fraud Risk
Technology has emerged as a powerful ally in the ongoing battle against invoice fraud, offering sophisticated tools and strategies that transform traditional financial protection methods. By leveraging advanced technological solutions, businesses can create robust defense mechanisms that proactively identify and mitigate potential fraudulent activities.
Artificial Intelligence and Machine Learning Detection
Artificial intelligence represents the frontline of modern fraud prevention. According to the U.S. Department of the Treasury’s Office of Payment Integrity, machine learning AI systems have successfully prevented and recovered billions of dollars in fraudulent payments.
Key AI-powered detection strategies include:
- Pattern Recognition: Analyzing historical transaction data to identify anomalous behaviors
- Predictive Modeling: Forecasting potential fraud risks before transactions occur
- Real-Time Monitoring: Instantaneously flagging suspicious invoice characteristics
- Adaptive Learning: Continuously improving fraud detection algorithms based on new data
These intelligent systems can process vast amounts of financial data exponentially faster than human analysts, detecting subtle irregularities that might escape traditional review processes.
Advanced Verification and Authentication Technologies
The Association for Financial Professionals recommends automated accounts payable processes that integrate multiple verification technologies. Modern authentication methods go far beyond simple password protection.
Cutting-edge verification technologies include:
- Blockchain Verification: Creating immutable, transparent transaction records
- Biometric Authentication: Using facial recognition or fingerprint scanning for financial approvals
- Multi-Factor Authentication: Requiring multiple independent verification steps
- Digital Signature Validation: Cryptographically confirming document authenticity
These technologies create complex, interconnected verification layers that significantly reduce the likelihood of fraudulent invoice submissions.
Comprehensive Digital Fraud Prevention Ecosystem
Modern technological approaches transform fraud prevention from a reactive to a proactive strategy. Learn more about comprehensive invoice data management that integrates advanced security technologies.
Comprehensive digital prevention strategies encompass:
- Cloud-Based Security Systems: Secure, encrypted storage with restricted access
- Automated Compliance Checks: Instant verification against regulatory standards
- Cross-Platform Integration: Seamless communication between financial systems
- Continuous Risk Assessment: Dynamic evaluation of potential fraud vulnerabilities
The Cash Management Leadership Institute emphasizes that technological solutions are not just about prevention but creating an adaptive, intelligent financial ecosystem.
Technology is rapidly transforming invoice fraud prevention from a manual, error-prone process to a sophisticated, intelligent system. By embracing these advanced technological solutions, businesses can stay several steps ahead of potential fraudsters, protecting their financial integrity with unprecedented precision and efficiency.
Frequently Asked Questions
How can businesses recognize invoice fraud?
Businesses can recognize invoice fraud by being aware of common schemes such as phantom vendor schemes, invoice alterations, and advanced digital fraud techniques. Regular training and vigilance in verifying invoices can also help in spotting potential fraud.
What steps should be taken to verify invoices?
To verify invoices, businesses should establish rigorous verification protocols, including vendor authentication, cross-referencing invoices with purchase orders, and confirming vendor contact information. Implementing a ‘Pause, Verify, Report’ (PVR) procedure is also recommended to ensure thorough validation before payment.
What role does technology play in preventing invoice fraud?
Technology plays a crucial role in preventing invoice fraud by utilizing artificial intelligence and machine learning to detect anomalies, leveraging secure document verification systems, and automating the approval process. These tools help in identifying suspicious activities before payments are made.
Why is segregation of duties important in preventing fraud?
Segregation of duties is important in preventing fraud as it ensures that no single individual has complete control over financial transactions, reducing the risk of collusion and unauthorized actions. This practice creates a system of checks and balances, enhancing overall financial security.
Ready to Stop Invoice Fraud Before It Starts?
Struggling with errors slipping through, fake vendors, or altered invoices? You are not alone. This article shows how easily a single fraudulent invoice can sidestep tired employees and outdated systems. Your business deserves better protection and peace of mind. Automated AI-powered verification is now within reach. By turning to Invoice Parse, you get technology specifically designed to reveal suspicious patterns, extract accurate vendor data, and streamline invoice processing according to the best practices outlined above.
See what seamless, secure, and reliable invoice handling looks like. Start transforming your invoice workflow in minutes with Invoice Parse today. Experience direct upload of your documents, instant detection of errors or inconsistencies, and easy integration with your data tools. Take control and outsmart fraudsters by trying our platform now at https://www.invoice-parse.com.
